Identity and Management
An EVIDIAN Success storyBy Thierry Winter
EVIDIAN has always focused its ITEA participation
within a track for controlling the access of users to the information system at large.
In the early 2000s, EVIDIAN held the view that investment by organisations in security
issues was going to increase, and that Identity and
Access Management (IAM) in
particular would become an important element in governing security.
Many analysts, such as Gartner in the US or KuppingerCole in Europe, created specific
sectors of security to monitor Identity and Access Management. They confirmed that
investment by organisations in IAM remained at a high level, growing in the period
2003-2016, despite the economic downturn observed in 2007-2009.
EVIDIAN has participated in or led ITEA projects in line with this vision in order to progressively create each essential function of infrastructure expected by the IAM market or to renew the obsolete existing technology by addressing, in turn, each limitation of the state-of-the-art. The illustration on the next page depicts the consistent affiliation between these related projects, involving a lot of expertise brought in by many participating partners.
Web Access Manager
In 2003, LASCOT played the role of evangelist for today's web protocols aiming at
interoperability of security operations. With LASCOT, EVIDIAN has added identity federation
functions to its web gateway, an innovative development conducted in the earlier PEPITA ITEA
Call 1 project. This opened up the world of web interoperability, turning the web gateway into
service provider and identity provider, at the heart of all interactions of social networks
today. While vendors of identity federation were just imagining future possible use cases, in
2005 EVIDIAN already had a pragmatic and realistic solution, Web Access Manager, deployed in a
wide intergovernmental organisation, or in four continental plates of a company in
'follow-the-sun' mode. Today, 300 installations are running Web Access Manager on four
continents. Customers welcome the efficiency, the adaptability to complex environments and the
inter-domain
capability of this solution, whose revenues were multiplied fivefold between 2005
and 2013.
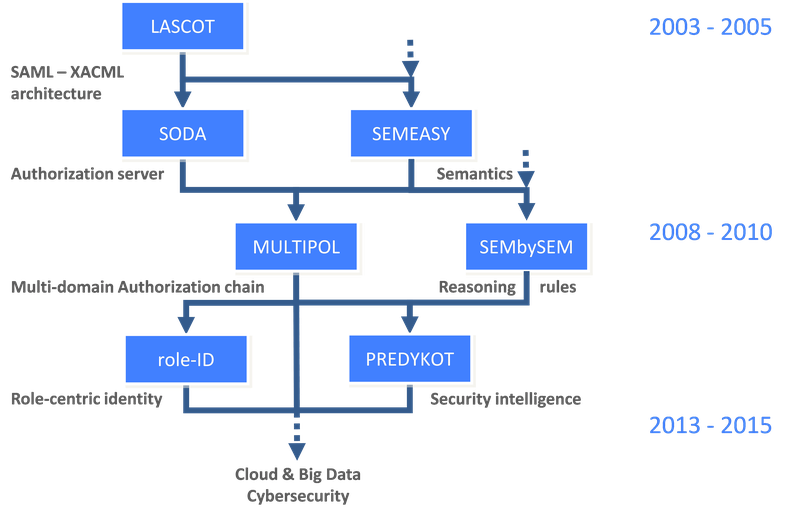
With SODA, EVIDIAN was looking for a solution for infrastructures that outsource access control. This principle helps application developers to focus on business functions and usually prevails in a service-oriented architecture, evident in the current SaaS trend. SODA indeed has applied this to the operation of industrial processes. EVIDIAN built a module to control the access to these processes, and derived from the project a generic authorisation server, expected to be heavily deployed in different sectors such as banking or industry.
To make it usable by security officers on a daily basis, MULTIPOL then integrated this authorisation server into the global access control chain. This crucial step centralises management of security policy, regardless of the approaches used for access control: dynamic, through the authorisation server, or by traditional provisioning of accounts in applications. To do so, EVIDIAN has added an application for governing security, which uses a policy model based on roles. MULTIPOL also benefited from the findings about semantics to achieve interoperation between the security policies of several independent domains.
Policy Manager
The Policy Manager application integrated in the EVIDIAN offer as a result of MULTIPOL is the control tower of the security policy of a company. It equips 200 customers in Europe and is deployed at 50 new customers every year. In addition, Policy Manager is progressively replacing 250 installations that have an older policy model.
However, initial deployments of the new access control chain have highlighted that the governance of security was now up to business people in organisations, and not to IT managers anymore. The Policy Manager application was originally intended for highly skilled personnel for the technical management of users and rights. EVIDIAN has therefore developed in role- ID and included in its solution a workflow-driven portal that allows employees and managers to request and validate updates to the security policy in order to manage the lifecycle of user rights. This operational 'user-centric' approach has become indispensable to any deployment of an access governance solution. The new Request Manager module that Evidian has integrated as a standard element of its IAM solution is now being installed at 20+ new customers every year
Security Intelligence
As a result, the previous IGA generation is being renewed smoothly, keeping these customers satisfied and boosting the revenue by 30% with new customers.
The Identity Governance & Administration (IGA) product line took off thanks to two breakthroughs which in fact needed to be simultaneous: finding an innovative model of security policy that is both powerful and flexible, developed in MULTIPOL, and backing it by a workflow oriented towards business users, itself controlled by policy, developed in role-ID. As a result, the previous IGA generation is being renewed smoothly, keeping these customers satisfied and boosting the revenue by 30% with new customers. Going one step beyond usual governance, PREDYKOT has found that these now complete mechanisms for applying a security policy do not ensure that security in companies is effectively in line with best practices. So PREDYKOT developed intelligent mechanisms precisely to help managers close the loop of the security policy, by proving that the desired rules are effectively applied in reality. For the project EVIDIAN developed new sensors, feeding new reasoning engines that provide dynamic feedback on security rules, with approval by security officers. By the end of 2014 EVIDIAN is going to introduce a first version of a new Security Intelligence solution that informs security officers about identified risks and non-compliance of access control rules. 65 risk situations can be reported so far and many correlation scenarios are under development. Built as an add-on to existing IAM infrastructures so that existing customers will leverage the investments they have already made, the new Security Intelligence features will be of interest to potentially 600 customer installations over the world. They will first consolidate the revenue of EVIDIAN's User Access Services product line, then form the basis of a new Security Intelligence solution.
"EVIDIAN is currently working on the prospect of applying these innovations to the fields of Cloud Computing, Big Data and Cyber-Security, inventing creative bridges between these domains," concludes Thierry Winter, ITEA project coordinator and EVIDIAN CTO.

